Table of Contents
Gain control over your network and navigate through real-time challenges with confidence, drawing from my own experience. Whether operating in the cloud, using a hybrid approach, or relying on on-premise solutions, Flowmon’s actionable intelligence empowers you. In my personal usage, Flowmon seamlessly integrates network operations (NetOps) and security operations (SecOps) into a unified, adaptable solution.
Experience the efficiency of automated traffic monitoring and threat detection with Flowmon, laying a robust foundation for informed decision-making. In my own encounters, Flowmon’s capability to sift through information noise has proven invaluable. Its intuitive interface enables IT professionals, like myself, to swiftly comprehend incidents and anomalies, delving into their context, impact, magnitude, and crucially, their root cause. This personal touch ensures that you are not overwhelmed by data but can instead focus on making effective and informed decisions in real-time.
Flowmon review
Flowmon is very important for keeping networks safe and visible. Its advanced tracking and analysis tools show network traffic in real time, which helps find and stop possible threats.
| Feature | Description |
|---|---|
| User Interface and Experience | Intuitive design for easy navigation, suitable for users of varying expertise. |
| Security Analytics | Robust tools for proactive threat detection and detailed insights into network behavior. |
| Performance and Bandwidth Management | Real-time monitoring and optimization tools for efficient resource allocation and reduced latency. |
| Customization and Scalability | Tailorable dashboards, reports, and alerts for adaptable network management; scalable architecture. |
| Integration Capabilities | Support for various deployment scenarios, including on-premises and cloud environments. |
| Reporting and Analytics | Comprehensive reporting features providing detailed insights into network performance and security. |
| visit website |
What is Flowmon?
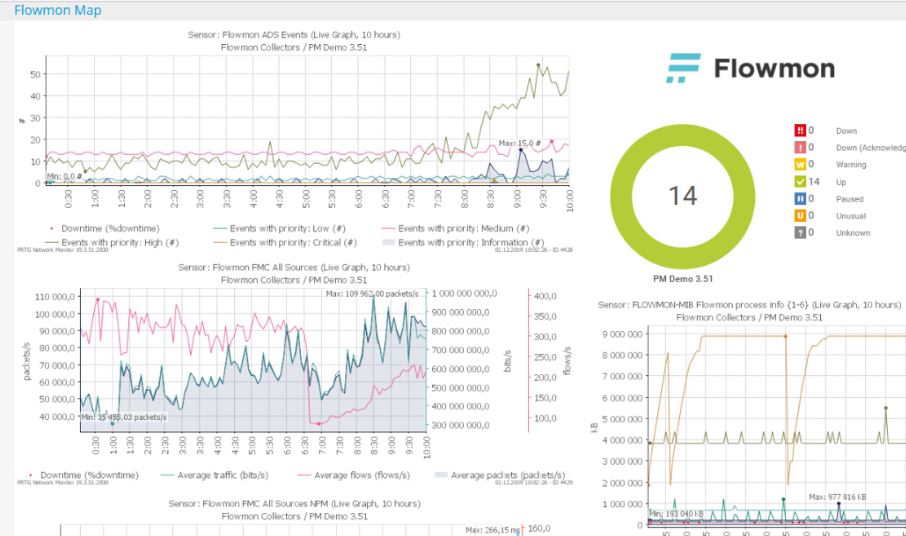
Flowmon has demonstrated itself to be an extraordinarily powerful and effective network monitoring and security tool in my own personal experience. When it comes to properly recognising possible dangers and giving a comprehensive understanding of network traffic, it has been a game-changer. It is distinguished from other solutions by the utilisation of flow-based network monitoring technology, which enables real-time analysis and visualisation of network behaviour.
The capability to deliver detailed insights on performance, bandwidth usage, and security events is one of the things that particularly stood out to me when I used it. The ability to proactively discover abnormalities, improve network performance, and fortify our cybersecurity defences has been significantly aided by this.
Flowmon review: User Interface and Experience
In my personal experience, Flowmon has proven to be an outstanding solution for network administrators seeking a user-friendly and seamless experience. The platform’s design is incredibly intuitive, ensuring that both newcomers and seasoned users can easily navigate through its features. Personally, I find the layout clear and the controls responsive, contributing significantly to enhanced efficiency in monitoring and managing network performance.
The visually intuitive dashboards and real-time analytics provided by Flowmon have played a crucial role in creating a positive user experience for me. These features enable quick identification and resolution of issues, empowering administrators to stay on top of network performance. Flowmon’s dedication to maintaining a streamlined and responsive user interface makes it a valuable tool, particularly for those looking for effective network monitoring and security analytics.
Flowmon review: Security Analytics in Flowmon
In my own experience, Flowmon has proven to be a standout in the realm of Security Analytics. It has served as a reliable and robust solution, effectively identifying and mitigating various security threats. What I appreciate most is its ability to offer comprehensive insights into network behavior, giving me the tools to proactively detect potential threats. The advanced anomaly detection and behavior analysis features have been instrumental in enhancing the overall security posture.
One aspect that stands out is Flowmon’s real-time alerts and detailed reports. These have empowered me as an administrator to respond promptly to potential security risks, ultimately contributing to a more resilient network. It’s reassuring to know that Flowmon’s Security Analytics goes beyond conventional security measures. Instead, it adopts a proactive approach to cybersecurity, which aligns well with the dynamic nature of evolving threats.
Flowmon review: Performance and Bandwidth Management
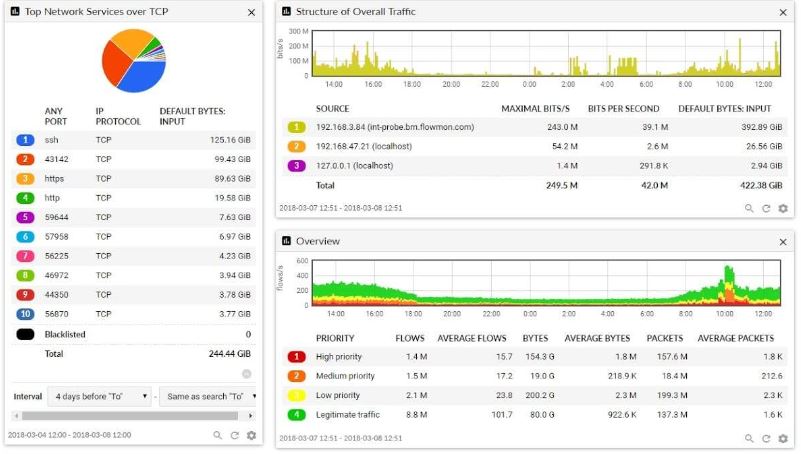
In my personal experience, Flowmon has proven to be a standout solution for managing performance and bandwidth effectively. It equips administrators with powerful tools that go a long way in optimizing network efficiency. The real-time monitoring capability of the platform provides valuable insights into how bandwidth is being used and the performance of various applications.
One of the key advantages I’ve found is the proactive identification and resolution of bottlenecks. This ensures that resources are allocated optimally, preventing potential slowdowns in the network. What sets Flowmon apart for me is its customizable dashboards and robust reporting features. These elements allow for precise management of network performance, ultimately reducing latency and enhancing the overall user experience.
Flowmon review: Customization and Scalability
When it comes to adapting solutions to match the specific requirements of various networks, in my experience, Flowmon has truly stepped out as a leader. When it comes to customising the platform to specific requirements that I’ve come across, the capabilities that allow for customization and scalability have been of the utmost importance. When I was an administrator, I found that being able to customise dashboards, reports, and alarms in accordance with the requirements of the network that I was administering was of tremendous benefit.
The scalable architecture of Flowmon is one of the features that I like and value the most. It has been demonstrated to be trustworthy in supporting the dynamic demands that come with developing networks, which ensures a high level of performance that is consistent throughout. As the network has developed over the course of time, the value of this adaptability has been increasingly apparent.
Final Words
In my personal experience, Flowmon has proven to be an impressive network monitoring solution that stands out in areas such as Security Analytics, Performance and Bandwidth Management, and Customization and Scalability. I’ve found its intuitive interface to be user-friendly, accommodating individuals with different levels of expertise.
The robust features of Flowmon go beyond just monitoring; they offer valuable insights for staying ahead of potential threats and optimizing network performance. What I appreciate most is Flowmon’s commitment to customization, which has allowed me to tailor the platform to my organization’s unique requirements. This adaptability ensures that the system can scale with our growing needs and stay relevant in the ever-evolving landscape of network technology.
Flowmon review: The good and The bad
The Flowmon system delivers superior-quality flow records in addition to unparalleled protocol visibility.
The Good
- Robust Security Analytics
- Efficient Performance Management
The Bad
- Learning Curve
Questions and Answers
Flowmon is a flow-based network performance tracking tool that keeps track of how much bandwidth is being used. It also helps IT understand how their traffic is structured and use this knowledge to find the source of network issues that happen on-premises, at the edge, or in the cloud.
The following things can be shown in a data flow diagram: places where data is stored (data at rest), especially sensitive data, and places where data moves between systems and tools (data in transit). Applications can share data with each other. Links to network models that show how the internal and external connections work.

