Table of Contents
From what I’ve seen, the main idea behind “Best Data Masking Tools” is to change private data into a form that is less sensitive but still works. This transformation is important for a number of application testing situations that require accurate and consistent data, as well as for analytics projects that use aggregated data for tasks like scoring, model development, and statistical reporting. New technologies keep coming out in the ever-changing world of data protection solutions, especially in the area of data hiding.
These technologies are made to redact, anonymize, pseudonymize, or use other methods to remove personal information from data. The main goal is to protect data from risks to privacy or security. In the field of “Best Data Masking Tools,” the main goal is to make sure that private information can be changed in ways that make it less sensitive while keeping its usefulness. These tools are important because they help meet the specific needs of application testing, where the data must be both accurate and useful.
They also play a key role in supporting analytical jobs that use collected data for things like scoring, making models, and reporting statistics. The market for data protection tools, which includes the best data concealment tools, is always changing. This is because new, cutting-edge technologies make it easier to remove personal information from data by redacting, anonymizing, pseudonymizing, or using other methods. The main purpose of these tools is still to improve data security by reducing risks to privacy and confidentiality.
Best Data Masking Tools Comparison Table
Data masking technologies are used to hide sensitive data during operations that are not part of production. This makes sure that laws like GDPR and HIPAA are followed. By hiding personal or confidential data, companies can test, analyze, or look into things without putting sensitive information at risk.
| Feature | Primary Use Case | Integration with Other Systems | Security Features | Scalability | Mobile-Friendly | Data Discovery | Website Link |
|---|---|---|---|---|---|---|---|
| SQL Server | Relational Database | Strong Microsoft Integration | Advanced | Scalable | Limited | No | Visit Website |
| Mage Platform | E-commerce Platform | N/A | Basic | Varies | Yes | N/A | Visit Website |
| Oracle Data Safe | Data Security in Oracle Cloud | Oracle Cloud Integration | Advanced | Scalable | N/A | Yes | Visit Website |
| Satori Data Security Platform | Data Privacy Compliance | Requires Integration | Comprehensive | Varies | N/A | Yes | Visit Website |
| DATPROF | Data Masking & Testing | Requires Integration | Moderate | Varies | N/A | Limited | Visit Website |
List of the Best Data Masking Tools
Tools for hiding data can be used in many different fields, such as healthcare, banking, retail, and more. They are used to make data anonymous for software development and testing, to keep customer data safe during analytics and research, and to follow laws about data security.
SQL Server

| Feature | Description |
|---|---|
| Robust Relational Database | A powerful relational database management system. |
| Integration with Microsoft | Seamlessly integrates with other Microsoft products. |
| Scalability | Scales to meet the needs of small to large systems. |
| Security Features | Offers advanced security features for data protection. |
| Visit Website |
SQL Server stands out because it has a wide range of goods that add to its main functions. These goods make SQL Server much easier to use because they have an easy-to-understand user interface. SQL Server has strong security features that make sure data is always protected, even when changing encrypted data. Dynamic data filtering, in particular, is very important because it hides personal information from people who shouldn’t see it. This gives clients confidence that their private information is safe.
I’ve found that fast-growing companies are especially interested in this method because of how it works. Keeping data in silos or on disks can make it more likely that data will be lost or damaged, which could be very bad for the company. With this program, data in every file is encrypted, making it very safe and professional. This is especially comforting because problems can happen when data is saved in separate places or on hard drives.
The Good
- Reliable and widely used.
- Strong integration with Microsoft ecosystem.
- Scalable to handle various workloads.
The Bad
- Licensing costs can be high.
Mage Platform

| Feature | Description |
|---|---|
| E-commerce Solution | A versatile e-commerce platform for online businesses. |
| Customization Options | Provides extensive customization capabilities. |
| Mobile-Friendly | Ensures a responsive and mobile-friendly storefront. |
| Analytics and Reporting | Offers in-depth analytics and reporting features. |
My research has shown that the qualities that define this strategy make it particularly desirable to businesses that are experiencing rapid expansion. It is possible to raise the danger of data leaks or damage by storing information in isolated locations, such as silos or on disks.
This might be extremely devastating to the company. Data in any format can be encrypted with the help of this application, making the process extremely trustworthy and reliable. This is especially encouraging given the potential for problems to occur if data is kept in disconnected locations or on physical disks.
The Good
- Excellent e-commerce capabilities.
- Highly customizable to suit specific business needs.
- Mobile-responsive design.
The Bad
- May require technical expertise for advanced customization.
Oracle Data Safe
| Feature | Description |
|---|---|
| Data Security | Focuses on securing sensitive data in Oracle Cloud. |
| Security Assessment | Conducts security assessments and identifies risks. |
| User Activity Monitoring | Monitors user activity for suspicious behavior. |
| Data Masking | Offers data masking to protect sensitive information. |
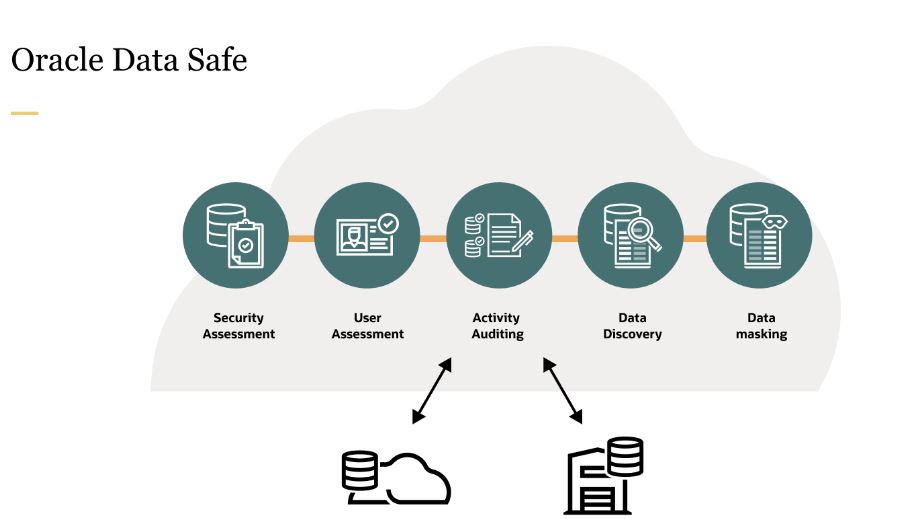
Data Safe acts as a centralized control center for Oracle Databases. It provides assistance in comprehending the sensitivity of data, evaluating data-related risks, masking sensitive data, implementing and monitoring security measures, assessing user security, monitoring user activity, and complying with data security regulations.
Data Safe was developed by Oracle. Data Safe is able to deliver key data security features on Oracle Cloud Infrastructure, regardless of whether the user is employing Oracle Autonomous Database or Oracle Database Cloud Service.
The Good
- Specialized in securing Oracle Cloud data.
- Provides comprehensive security assessments.
- Monitors user activity effectively.
The Bad
- Primarily suited for Oracle Cloud users.
Satori Data Security Platform

| Feature | Description |
|---|---|
| Data Privacy Compliance | Helps organizations comply with data privacy regulations. |
| Data Discovery | Discovers sensitive data across the organization. |
| Access Controls | Manages access and permissions for data protection. |
| Data Masking | Offers data masking for privacy and security. |
Satori is a Data Security Platform (DSP) that makes it possible for users to access data and analytics on their own. In contrast to the more traditional methods of manually accessing data, users of Satori have access to a personal data portal that enables them to readily browse and retrieve all of the available datasets in a timely manner.
The dynamic security and access controls are applied by Satori’s DSP on the fly, which enables secure data access in a matter of seconds as opposed to weeks. In addition, the extensive DSP that Satori possesses enables all access, permissions, security, and compliance policies to be managed from a single console. Satori performs continuous monitoring of sensitive data across all storage sites, dynamic tracking of how the data is used, and necessary protection measures are applied.
The Good
- Facilitates data privacy compliance efforts.
- Effective data discovery capabilities.
- Robust access control features.
The Bad
- May require integration with existing systems.
DATPROF

| Feature | Description |
|---|---|
| Data Masking | Specializes in data masking and obfuscation. |
| Test Data Generation | Generates realistic test data for software testing. |
| Data Subset | Creates subsets of production data for development. |
| Data Compliance | Helps meet data compliance requirements. |
The DATPROF Data Masking application is really helpful, in my experience, when conducting efficient testing on databases. It features a patented way for properly subsetting the database, which makes it an effective method for data provisioning and masking, both of which are efficient approaches.
Despite having a straightforward interface, the application is exceptional when it comes to managing intricate data relationships. Its innovative approach to evading triggers, limitations, and indices has shown to be the most successful solution available on the market, which is a huge benefit, and this is the reason why it has become the most popular option.
The Good
- Focuses on data masking and test data generation.
- Simplifies the generation of realistic test data.
- Enables efficient data subset creation.
The Bad
- Limited features beyond data masking and test data generation.
Use Cases for Data Masking
Data masking is very important in many situations and businesses where protecting sensitive data is very important. Here are a few popular ways that data masking is used:
- Making software and testing it: When making software, writers often need access to real-world data for testing and fixing bugs. Data masking helps developers work with real-world datasets without putting security or privacy at risk by replacing private production data with fake or scrambled information.
- Business Intelligence and Analytics: Data scientists and people who work in business intelligence need access to data in order to draw conclusions and make reports. Data masking lets people share datasets while keeping their privacy and making sure that private information stays hidden.
- Compliance with rules and regulations: Businesses in many fields, like healthcare (HIPAA), finance (PCI DSS), and those governed by GDPR, have to protect private data. Data masking helps companies follow these rules by hiding or making personal and financial information look like something else.
How to Choose the Right Data Masking Tool?
Organizations that want to protect private data while keeping it usable must choose the right data masking tool. Here’s a step-by-step plan to making a good decision:
- Figure out what you need: First, figure out what your organization’s unique data masking needs are. Find out what kinds of data you need to protect, such as personally identifiable information (PII), banking data, or health records.
- Considerations for compliance: Find out what data security rules apply to your business or area, such as GDPR or HIPAA. Make sure that the data masking tool meets these standards for compliance.
- Evaluate techniques for hiding: Different tools for hiding data use different methods, like replacement, shuffling, or tokenization. Check to see which masking methods work best for your info and your security goals.
Questions and Answers
A: The best data masking tools should have features like advanced masking methods, support for different types of data (structured and unstructured), scalability, role-based access control, data discovery and classification, data lineage tracking, and integration with existing data infrastructure.
A: Delphix, Informatica Data hiding, IBM Guardium, Oracle Data Masking and Subsetting, and Redgate Data Masker are all well-known tools for hiding data. The tool you choose will depend on your unique needs and the infrastructure you already have.
A: Both data filtering and encryption are ways to keep information safe, but they do so in different ways. Data masking hides private information by giving it fake or changed values. This lets it be used for testing and development without giving up privacy. Encryption, on the other hand, changes data into a code that can’t be read. To get to the original data, you need to decrypt it. Encryption is used to store and send data in a safe way.

