Table of Contents
VeraCrypt is a great application for encrypting data, and I’ve had the pleasure of using it. Mounir Idrassi, the principal developer, and a dedicated volunteer developer are the only people who have made significant contributions to the project. In addition to being free and open source, it also has a fascinating history that involves only these two people. VeraCrypt is a powerful contender in the field of encryption software despite the fact that its primary purpose is to protect the files on a local computer. The program’s feature set is surprisingly robust, and this helps it fulfill its primary purpose.
VeraCrypt’s origins may be traced back to TrueCrypt, an additional open-source encryption application that was, sadly, eventually terminated. This is an important component of VeraCrypt’s history. VeraCrypt was developed by Mounir Idrassi using the source code of TrueCrypt, but with several of its security features upgraded. VeraCrypt is, in point of fact, one of the most impressive alternatives to TrueCrypt, based on my personal experience. When it comes to encryption software, it continues to be among the most recommended options, despite the fact that it might not be the best option for the typical end user.
The vast customization options provided by VeraCrypt are what set it apart from other encryption software. These choices provide you the ability to encrypt and store your information in exactly the manner that best suits your needs. In addition, VeraCrypt includes a number of innovative features that, speaking from my own point of view, cannot be compared to anything else that I’ve encountered in other forms of encryption software.
VeraCrypt Specifications
VeraCrypt is an effective and flexible disk encryption application that provides users with a comprehensive collection of functionality and customization possibilities. It is a fantastic option for both individuals and companies that need to prevent illegal access to their data, and both types of users can benefit from using it.
| Feature | Specification |
|---|---|
| Encryption algorithms | AES, Serpent, Twofish, Camellia, Rijndael, and ChaCha20 |
| Block cipher modes of operation | XTS |
| Key derivation functions | PBKDF2 with RIPEMD-160, SHA-256, SHA-512, Streebog, or Whirlpool |
| Hash functions | RIPEMD-160, SHA-256, SHA-512, Streebog, or Whirlpool |
| Maximum volume size | 8,589,934,592 GB (2 63 bytes) |
| Download Now |
What is VeraCrypt?
Mounir Idrassi developed VeraCrypt, an open-source encryption program. Mounir based VeraCrypt on TrueCrypt, another open-source encryption application. He built VeraCrypt a popular encryption program by improving its features. VeraCrypt lets you work with sensitive data easily, keep your computer protected from illegal access, and keep your data private.
The key difference between TrueCrypt and VeraCrypt is that VeraCrypt solves various security and vulnerability risks that TrueCrypt suffered from. Let’s explain TrueCrypt and VeraCrypt’s primary differences. TrueCrypt utilizes 1000 iterations for PBKDF2-RIPEMD160, while VeraCrypt uses 327661. Is VeraCrypt better than TrueCrypt? Yes. VeraCrypt is better than TrueCrypt but not the best encryption tool.
VeraCrypt review: Plans and pricing
Since VeraCrypt is distributed as freeware, there is no fee associated with downloading or using it. You are able to make financial contributions to the endeavor using a variety of channels, including Bitcoin, Bitcoin Cash, Ethereum, Litecoin, and Monero, as well as PayPal, bank transfers, Liberapay, and Flattr.
VeraCrypt review: Rescue Disk
Unfortunately, the encryption of the system could result in some problems. In the event that there is a problem with the launcher, your computer will not boot, and you will have no access to the system at all. VeraCrypt, fortunately, includes a failsafe in its software. You have the option of creating a rescue disk whenever you encrypt a system partition or drive. This disk can be saved on a CD/DVD or USB drive, depending on your preference.
If the VeraCrypt Boot Loader has been corrupted for whatever reason, or if data that is related to decryption has been lost, your rescue disk can restore those issues and allow you to regain access. You are strongly encouraged to construct a recovery CD; but, doing so is accompanied by a number of important caveats. If you want to make sure that you are safe, you should read the writeup that VeraCrypt has provided for the functionality.
VeraCrypt review: Hidden Volume
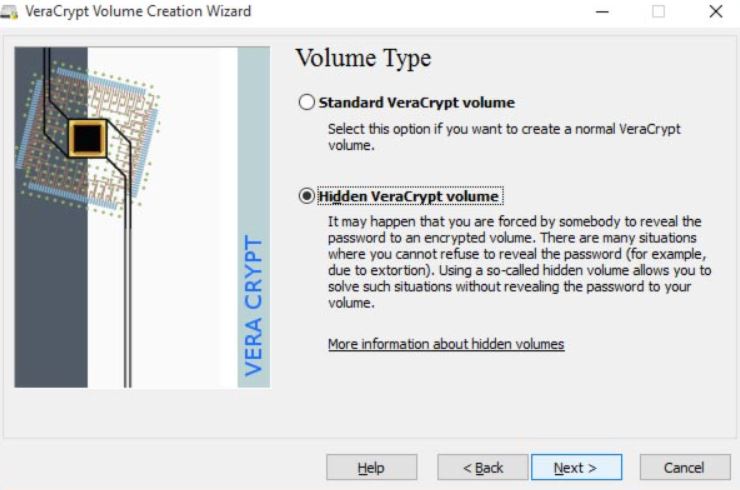
The term “Hidden Volume” refers to precisely what it sounds like: a volume that is concealed. Do not confuse this feature with the “hidden operating system,” since that is an entirely separate and distinct function. The term “Hidden Volume” refers to a partition that is kept concealed within an ordinary encrypted disk. A standard encrypted volume is a volume that is viewable but is nonetheless encrypted and secure even when it has not been password protected.
despite the fact that this secret volume is “inside” the regular volume. There is no way to verify that the concealed volume actually exists because it is hidden “behind” the usual encryption. This is what gives you the ability to maintain a believable denial. That is to say, there is no evidence to suggest that the concealed volume genuinely exists beneath the conventional volume; hence, you are free to entirely disclaim any prior knowledge of such a volume.
VeraCrypt review: The Power of Plausible Deniability
Probable deniability is one of VeraCrypt’s biggest advantages. Thus, you can deny having important information on your computer because it’s impossible to establish. Encrypting your data may lead the accuser to believe you are protecting anything sensitive. It cannot be proven. VeraCrypt lets you hide a volume inside an invisible volume for plausible deniability. Create an encrypted OS with VeraCrypt. No way to establish a secret disk or operating system exists, therefore plausible deniability. A VeraCrypt-encrypted device or partition will contain random data without a signature. It’s nearly impossible to establish a VeraCrypt volume is an encrypted partition or device.
VeraCrypt review: Interface and in use
VeraCrypt’s use requires significantly more attention to detail than, say, Microsoft BitLocker’s, and this is mostly due to the increased number of available customization choices. However, the installation of VeraCrypt is accomplished by navigating through its step-by-step wizards, which provide exemplary direction at each stage of the process.
The user interface provides access to a number of additional helpful functions, such as an encryption benchmark tool, a disk expander, and a keyfile generator. You’ll find a comprehensive list of configuration options for customizing VeraCrypt to your exact specifications in the preferences section of the program.
Final Words
VeraCrypt is a fantastic piece of software that you may use to protect the privacy of your critical files. VeraCrypt may become more difficult to use when the number of systems and users who are engaged increases because it does not have a centralized server for authentication and it does not have built-in support for cloud storage. However, the number of potential attack vectors can be decreased by excluding these functionalities from the software.
Its nifty features, which include file-based virtual drives with on-the-fly encryption, hidden volumes with different passwords, and system encryption with on-boot authentication, make it an exceptionally helpful and free application for anyone who is interested in encrypting files.
VeraCrypt review: The Good and Bad
VeraCrypt is not only an outstanding tool for creating virtual encrypted disks and partitions, but it is also one of the best ways to encrypt a complete operating system to keep your valuable files safe, secure, and secret. VeraCrypt is an excellent tool for creating virtual encrypted disks and partitions.
The Good
- Free
- Multiple encryption options
The Bad
- No support for cloud storage
Questions and Answers
On-the-fly encryption keys, also known as OTF keys, are VeraCrypt and all other crypto containers’ one and only point of failure, with the exception of disks encrypted with Apple T2 chips. While the encrypted disk is mounted, the key to the binary encryption used for the symmetric encryption is kept in the volatile memory of the machine at all times.
When looking at possible alternatives to VeraCrypt, customer data and files are two more key aspects to take into consideration. We have created a list of solutions that reviewers voted as the best overall alternatives and competitors to VeraCrypt. These solutions include GnuPG, FileVault, and Microsoft’s BitLocker, amongst others.

